Internet culture stood as an antithesis to Bell telephone culture. In the early 1960s,
Paul Baran, who was concerned about the vulnerability of U.S. communications, advocated that the Department of Defense migrate to a distributed packet-switched network that could survive failure and still get a “Go; No-Go” command to the field. Bell-trained DOD engineers dismissed packet-switched communications as an idea that could not possibly work. In
1971, Larry Roberts, having successfully demonstrated the viability of his packet-switched network experiment, attempted to give ARPANET to AT&T; AT&T was not interested. In the meantime,
AT&T had refused to sell private lines to nascent data networks, refused to allow
foreign devices (i.e., modems) to their network, and
refused to interconnect their network with nascent rivals. Those seeking telecommunications services in order to build computer networks became frustrated, and serious question arose concerning
whether AT&T’s telecommunications services would meet the needs of growing computer networks.
Thus emerged a cultural rivalry between Nethead and Bellhead cultures. In the eyes of the Netheads, Bellheads were about perpetuating a century-old communications network monopoly that followed a command-and-control model of central operation which stunted innovation, while Netheads were all about innovation, building a network that fostered the cool things transpiring at the end. Netheads wanted nothing of the Bellhead model.
[Greenstein 2015 at 38 ("most had an almost visceral dislike for" Ma Bell)] [Mayo (quoting Bob Taylor, "Working with AT&T would be like working with Cro-Magnon man. I asked them if they wanted to be early members so they could learn technology as we went along. They said no. I said, Well, why not? And they said, Because packet switching won’t work. They were adamant.").]
In the 1980s, Netheads had to resolve how to interconnect networks. Netheads wanted to interconnect ARPANET with an NSF sponsored
CSNET, but what should be the terms and who should pay whom? One model before them was the byzantine Bell accounting scheme which one engineer described as so complicated it was akin to drinking coffee one molecule at a time; a marvelous feat of engineering if not utterly pointless.
[Moore 1999] [Jacobson 1999 (discussing how Internet culture is different than BellHead culture and the implications for the future of the internet)] [Kleinrock 1994 at 67 (bemoaning the additional cost and complexity of accounting necessary for usage-based pricing); [MacKie-Mason 1993 at 14 (describing the cost of phone company style billing and accounting as applied to the packet-switched Internet as “astronomical”).] Netheads' incentive was to grow network effect and continue innovation at the ends. To achieve that incentive, they wanted the lowest possible barriers to the expansion of the network. The solution was settlement-free interconnection, devoid of complicated Bell accounting. A paper by Lyman Chapman and Chris Owens describes how the arrangement came to be:
In modern terms, we would say that the customers of one ISP (ARPAnet) could not communicate with the customers of another ISP (CSNet), because no mechanism existed to reconcile the different Acceptable Use Policies of the two networks. This disconnect persisted as both sides assumed that any agreement to exchange traffic would necessarily involve the settlement of administrative, financial, contractual, and a host of other issues, the bureaucratic complexity of which daunted even the most fervent advocates of interconnection—until the CSNet managers came up with the idea that we now call “peering,” or interconnection without explicit accounting or settlement. A landmark agreement between NSF and ARPA allowed NSF grantees and affiliated industry research labs access to ARPAnet, as long as no commercial traffic flowed through ARPAnet.
NSF followed CSNET's example for interconnection settlements; interconnections between NSFNET and regional networks was on a settlement-free basis. [MacKie-Mason 1993 at 18 (“The full costs of NSFNET have been paid by NSF, IBM, MCI and the State of Michigan”).]
Commercial networks emerged in the early 1990s,
but they could not exchange traffic through the academic NSFNET. On the one hand,
Advanced Network Services(ANS), the contractor that operated the
NSFNET, established a commercial backbone service and offered to sell interconnection to nascent commercial networks. ANS had all of the NSFNET clients as end-users including regional networks and academic networks; ANS as the largest network could leverage network effect. But the other commercial networks were not interested in paying ANS for the right to access end-users or helping ANS become the AT&T-monopoly of the Internet. Instead they established the
Commercial Internet eXchange (CIX) and exchanged traffic on a settlement-free basis. For these early commercial networks, connectivity was paramount and growth of access services was king.
[Brock, Economics of Interconnection at ii ("Commercial Internet service providers agreed that interchange of traffic among them was of mutual benefit and that each should accept traffic from the other without settlements payments or interconnection charges. The CIX members therefore agreed to exchange traffic on a "sender keep all" basis in which each provider charges it own customers for originating traffic and agrees to terminate traffic for other providers without charge.").] First
UUNET,
PSINET, and
CERFNET joined CIX. Then
Sprint joined. Soon most of the Internet could be reached through CIX. Connectivity grew network-effect which grew the value of the access service that these commercial networks were selling to end-users. CIX become the model of commercial interconnection, while ANS became isolated.
[Greenstein 2015 at 81 ("Just a little less than a year later, CIX essentially had everyone except ANS. By the time Boucher held his hearing, ANS had become isolated, substantially eroding their negotiating leverage with others. By June 1992 ANS's settlement proposals no longer appeared viable. In a very public surrender of its strategy, it agreed to interconnect with the CIX on a seemingly short-term basis and retained the right to leave on a moment's notice.)] [Noam 2001 at 63 (""Soon the relative use by the commercial and nonprofit sectors kept shifting, and the power over interconnection moved to the former. By 1993, approximately 80 percent of all Internet sites could be accessed outside the NSFNET structure. CIX blocked ANS traffic from routing through the CIX router, thus depriving ANS users of connectivity to CIX members. Humbled, ANS joined CIX in 1994"")] [Srinagesh at 143 ("In October 1993, CIX, apparently without warning, blocked ANS traffic from transiting the CIX router. At this point, ANS (through its subsidiary CO-RE) joined the CIX and full connectivity was restored.")]. In 1994, ANS' assets were sold off to AOL.
[History, Advanced Network Services (2004)] [Salus 1995 at 200]
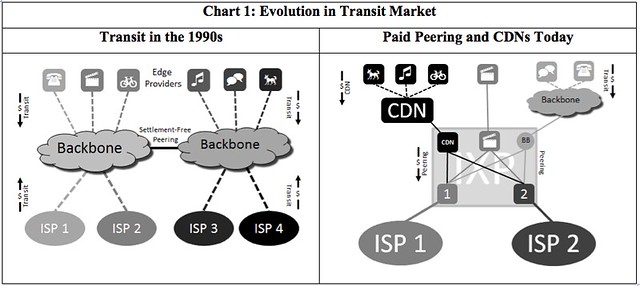
In the late 1990s, academic and government networks focused on research, development, and innovation, not commercial competition; they followed
settlement-free peering as a simple accounting scheme for interconnection. Commercial backbone providers adopted settlement-free peering as a means of rapidly growing their business plans.
Access networks, which needed to provide full Internet service to their customers, interconnected with and paid
transit to commercial backbone providers. Controversy swirled during the late 1990s as the commercial backbones matured their business plans, converting smaller networks that were dependant on the backbone networks' services from settlement-free peers into paying transit customers. Appeals for intervention reached the FCC,
which declined to intercede, finding the Internet backbone market competitive.